AES
AES-128-ECB and AES-128-CBC
Here 128 refers to number of bits.
128 bits = 16 bytes
Block
AES has to be applied on blocks of input data. Each block is of 16 bytes length.
2D Matrix Representation
16 bytes block can be represented in a 4 x 4 matrix. Example: “YELLOW SUBMARINE” can be represented as:
'Y' 'O' 'U' 'R'
'E' 'W' 'B' 'I'
'L' 'M' 'N'
'L' 'S' 'A' 'E'
Note: Bytes has to be filled columnwise and not rowwise. Aim is to spread out the message. This is one of the ideas of crypto DIFFUSION.
Operations
Encryption Decryption
---------- ----------
addRoundKey addRoundKey
subBytes invSubBytes
shiftRows invShiftRows
mixColumns invMixColumns
Details about these operations can be found in my friend’s blog here.
Block Cipher Encryption + Decryption
message = decrypt(encrypt(message))
As it is clear from the expression, decryption is the reverse of encryption. Once you understand encryption, just reverse the steps you have done in encryption and you will get decryption.
Key expansion
Block cipher encryption/decryption consists of multiple rounds of operations. Each time you apply addRoundKey() operation, it needs a different key to be added.
Given an initial key, say k of length 16 bytes, we can apply a procedure to get expanded keys. As we will see later, in block cipher operation addRoundKey() is applied 11 times. We will use key expansion procedure to get 10 new keys.
key k
key k1 = expandKey(k)
key k2 = expandKey(k1)
.
.
.
key k10 = expandKey(k9)
These keys k, k1, …, k10 has to be found in advance before starting with block cipher encryption and decryption process.
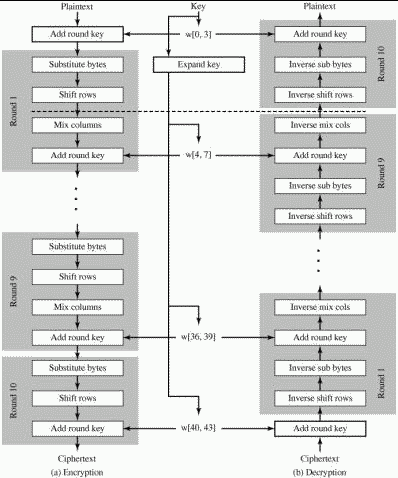
Block cipher encryption
begin =
addRoundKey
middle = 9 rounds
subBytes
shiftRows
mixColumns
addRoundKey
end =
subBytes
shiftRows
addRoundKey
Block cipher decryption
begin =
addRoundKey
middle =
invShiftRows
invSubBytes
addRoundKey
invMixColumns
end =
invShiftRows
invSubBytes
addRoundKey
Note: Following figure shows that block cipher decryption is just the reverse of block cipher encryption process.
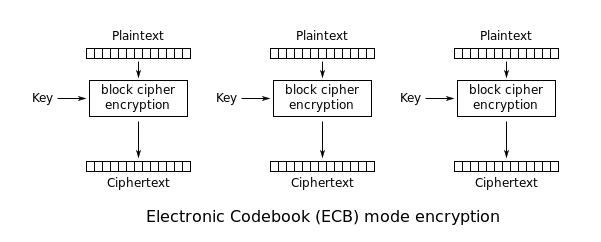
AES-128-ECB
Encryption
For each of the blocks, feed plaintext block and key to block cipher encryption and thats it. We will get ciphertext corresponding to each block of plaintext. Combine them and you are done!!!
Decryption
For each of the blocks, feed ciphertext block and key to block cipher decryption and thats it. We will get plaintext corresponding to each block of ciphertext. Combine them and you are done!!!

Note: In ECB mode, operations on each block of plaintext is independent of other blocks. This means two different blocks of similar plaintext will give same ciphertext. This fact related to duplicates can be misused to crack AES-ECB.
AES-128-CBC
CBC overcomes the problem in ECB mode. While performing block cipher encryption/decryption on a block, it depends upon the ciphertext of the previous block operation.
For the first block, we take initialization vector(IV). For rest of the blocks IV is the same as ciphertext of previous blocks.
Encryption
Before applying block cipher encryption process, perform plaintext xor IV.
Decryption
After applying block cipher decryption process, perform output xor IV to get plaintext.

PKCS#7 Padding
The message to be encrypted can be of any length. To make sure that the length is a multiple of block size(16 bytes here), we will add PKCS#7 padding. Example, “YELLOW SUBMAR” will be changed to “YELLOW SUBMAR\u0003\u0003\u0003”. More details here.
Tools
Use openssl command line tool to encrypt/decrypt as per ECB and CBC modes.
Refer to post to understand usage.
Further reading
- Comic version A Stick Figure Guide to the Advanced Encryption Standard (AES)
- FIPS Document link
- Purdue University
- Youtube video